-

ITAM is an investment in cybersecurity, not a cost
In the following article, Rishi Simbudyal from Teqtivity explains why ITAM is so critical to cyber security, and why cybersecurity professionals need ITAM more than ever. According to IBM’s Cost of a Data Breach Report, the ... -
-
ITAMantics - April 2024
Welcome to the April 2024 edition of ITAMantics, our monthly news podcast where we discuss the biggest ITAM stories from ... -
Broadcom is removing expired VMware licences from its portal - take action now!
Hot on the heels of Broadcom’s announcement of the end of perpetual licences for VMware it has given customers barely ... -
Who Loses When Broadcom Wins?
News of a new Broadcom deal rarely arrives with great fanfare. The November 2023 VMware acquisition provoked open worry online ...
-
-
How to win at job interviews
We sit down with Damian Harris, Global Talent Acquisition Manager at ITAM Review Careers, to get some tips for smashing it in your next interview.
-

ITAM is an investment in cybersecurity, not a cost
In the following article, Rishi Simbudyal from Teqtivity explains why ITAM is so critical to cyber security, and why cybersecurity professionals need ITAM more than ever. According to IBM’s Cost of a Data Breach Report, the ... -
-
ITAMantics - April 2024
Welcome to the April 2024 edition of ITAMantics, our monthly news podcast where we discuss the biggest ITAM stories from ... -
Broadcom is removing expired VMware licences from its portal - take action now!
Hot on the heels of Broadcom’s announcement of the end of perpetual licences for VMware it has given customers barely ... -
Who Loses When Broadcom Wins?
News of a new Broadcom deal rarely arrives with great fanfare. The November 2023 VMware acquisition provoked open worry online ...
-
-
The Software Licensing of Robots
Robots are increasingly present in our day-to-day lives. If you thought licensing servers was difficult, imagine licensing devices of higher complexity that walk around and interact with the virtual and the physical world.
Can’t find what you’re looking for?
-
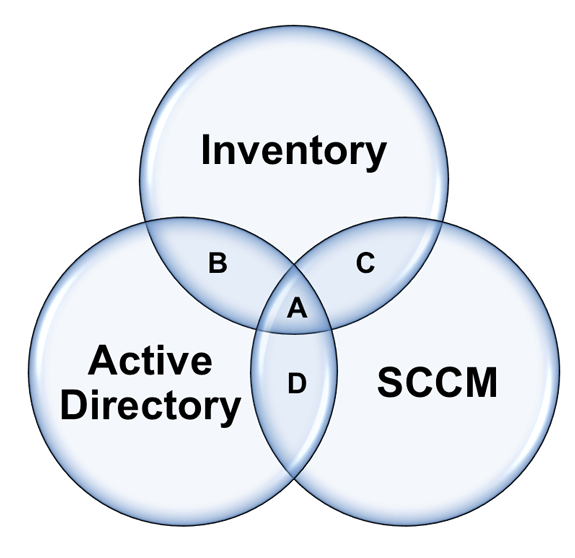
Verifying Asset Accuracy
A reader writes. “What is the industry standard way of calculating ITAM accuracy?” I’m not sure about the ‘industry standard’ way, but I’ll share techniques I’ve used in the past, hopefully others can chip in their ... -

Quick Guide to Mobile Device Management (MDM) Part 2 of 2
Recap We previously looked at what exactly mobile device management (MDM) is and the types of solutions available to organisations. In part two we dive deeper into MDM including how MDM can help support mobile devices, ... -

Quick guide to Hardware Asset Tagging
Martin Thompson and I were recently commissioned to write an overview of options for Hardware Asset Tagging for a client. The client has kindly let us share our report for the benefit of the ITAM Review ... -
Quick Guide to Mobile Device Management (MDM) Part 1 of 2
Mobile devices are increasing in popularity within organisations. With so many mobile device types and options currently on the market, organisations are spoilt for choice when choosing what tablet their employees can use, or what mobile ... -
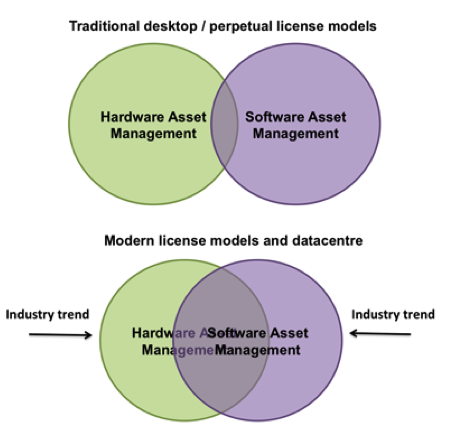
The convergence of SAM and HAM
This is part two of a two-part series on environment recognition. See part one here. ‘Modern SAM requires ‘Environment Recognition’ as much as ‘Software Recognition’. In my last article I explored the concept of ‘environment recognition’. ... -

How many machines, really?
The most common challenge we face when starting a new software / IT asset management project is obtaining reliable data on exactly how many assets we’re dealing with. Lack of visibility is the biggest challenge. In ... -

ISACA issues new BYOD audit programmes
ISACA has this month released news of more than 40 customisable IT audit/assurance programmes, which have been developed to help IT auditors who are facing increasing challenges brought about by “Bring Your Own Device” (BYOD) trends that ... -

3 Steps to Defining BYOD Policy
This article has been contributed by Stephen Midgley, Vice President Global Marketing at Absolute Software. In this article Stephen explains how to securely navigate the BYOD landscape. Recent research into mobile device deployment in the ... -

Mobile Device Management (MDM) Buyers Guide
I have been investigating technology that might enable a company to develop a ‘Bring Your Own Device (BYOD)’ policy or more advanced management of company owned tablets and mobile devices. The days of one or two corporate ... -

Old School Hard Drive Destruction [VIDEO]
I recently stumbled across this unique way of ensuring hard drives are destroyed. You might call it ‘labour intensive’, but at least you get to see the job done onsite and ensure no data leaks. Perhaps ...

